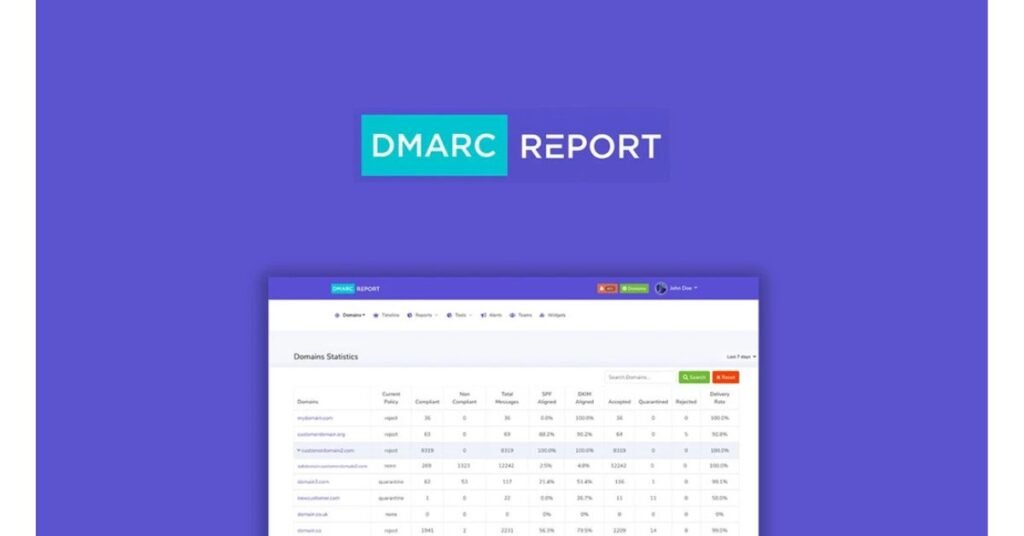
What is DMARC Report?
DMARC Report is an email authentication tool that enhances security by helping organizations detect and prevent email spoofing. It builds on two key standards. One is sender policy framework or SPF and another is domain keys identified mail or DKIM. With DMARC, domain owners gain control over who can send emails on behalf of their domain, reducing phishing risks.
Sold out now on Appsumo. Check – DMARC Report appsumo lifetime deal
DMARC report composed of following features:
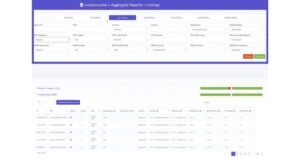
- Domain alignment verification
- Policy enforcement
- Reporting for visibility into email activity
- Sender policy framework integration
- Domain keys identified mail support
- Feedback on authentication outcomes
- Mitigation of phishing and spoofing attempts
- Aggregate and forensic reporting
- Customizable policy configurations
- Subdomain policy management
- Visibility into email delivery issues
Benefits of using DMARC report:
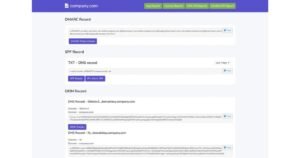
- Protects against phishing and spoofing
- Increase email deliverability
- Enhances domain reputation
- Provides visibility into email traffic
- Reduces spam reaching recipients
- Supports alignment with industry standards
- Builds trust with customers and partners
- Enable proactive threat response
- Offers detailed reports on email authentication
- Helps prevent unauthorized domain use
DMARC has the following applications:
- Validates sender identity through email authentication
- Aligns policies for domain protection
- Specifies actions for handling unauthenticated emails
- Generates feedback reports on email activity
- Detects and mitigates phishing attempts
- Prevents unauthorized email domain usage
- Enhances email visibility and control
- Supports compliance with security standards
- Protect brand reputation from email abuse
Find more Digital tools – Click here
DMARC report is essential for organizations to enhance their email security. By analyzing these reports businesses can identify and address potential vulnerabilities in their email authentication processes.